|
Product Introduction |  |
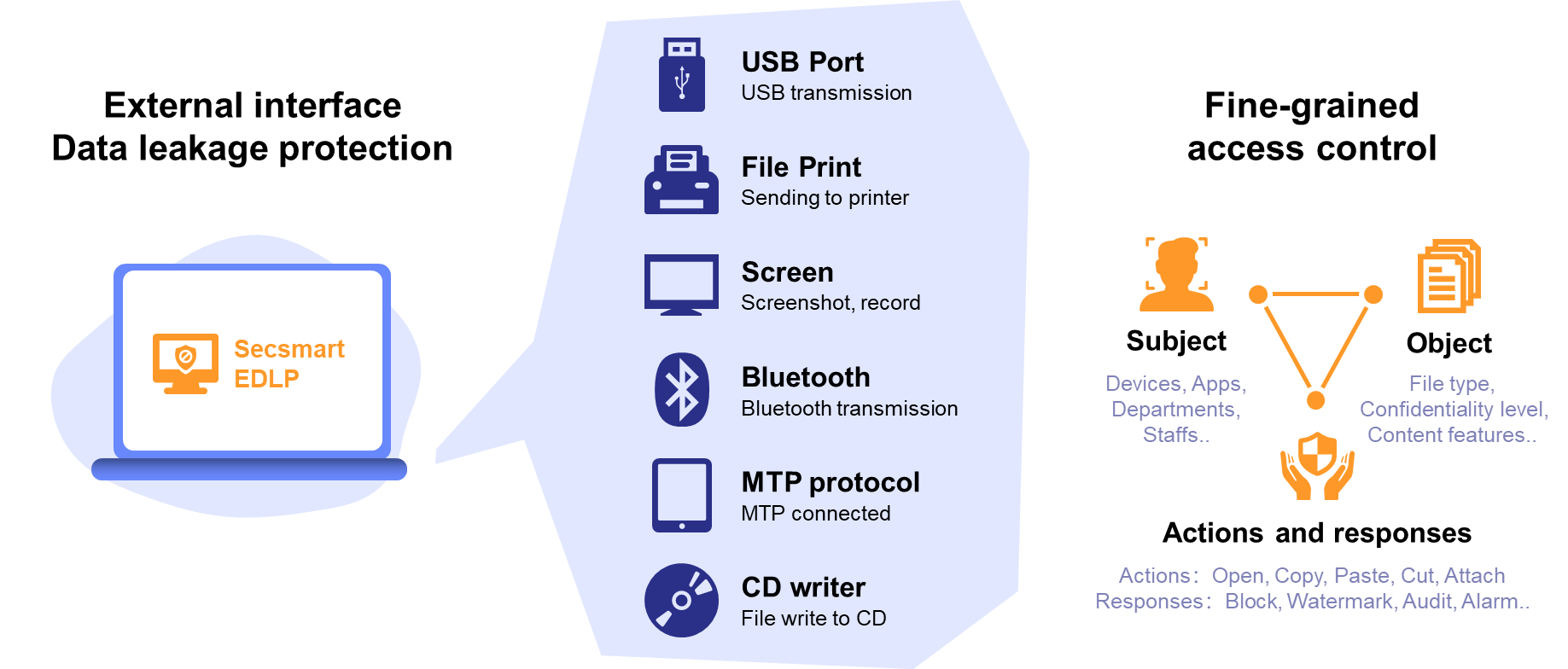
Secsmart Endpoint Data Leakage Prevention Product is deployed on endpoint computers, utilizing operating system-level technologies and integration mechanisms to monitor real-time leakage risks such as copying to USB drives, file printing, WeChat messages, screen capturing, email, and file uploads. It prevents unauthorized personnel from leaking sensitive data obtained from the endpoint and provides traceability for data that leaves the endpoint computer.
 |
Product Value |  |
 |
Deployment Mode |  |
Secsmart Endpoint Data Leakage Prevention Product is centrally managed by a management control platform. Endpoints automatically obtain corresponding policy information based on the settings of the management control platform. When using data, the endpoints match content according to the policy and activate response actions based on the policy settings to achieve the goal of data leak prevention.
 |
Product Advantages |  |
Recommended Products
Solutions
Contact Us