|
Product Introduction |  |
Secsmart Application Data Security Audit Product is a data security product positioned on the web application side, designed to assist users in organizing complex applications and interfaces, creating interface portraits and access trajectories, monitoring risks associated with sensitive data flow, identifying abnormal user behaviors in interface invocations, and providing data security assurance for the compliant and proper use and circulation of business data within application systems.
 |
Product Value |  |
 |
Deployment Mode |  |
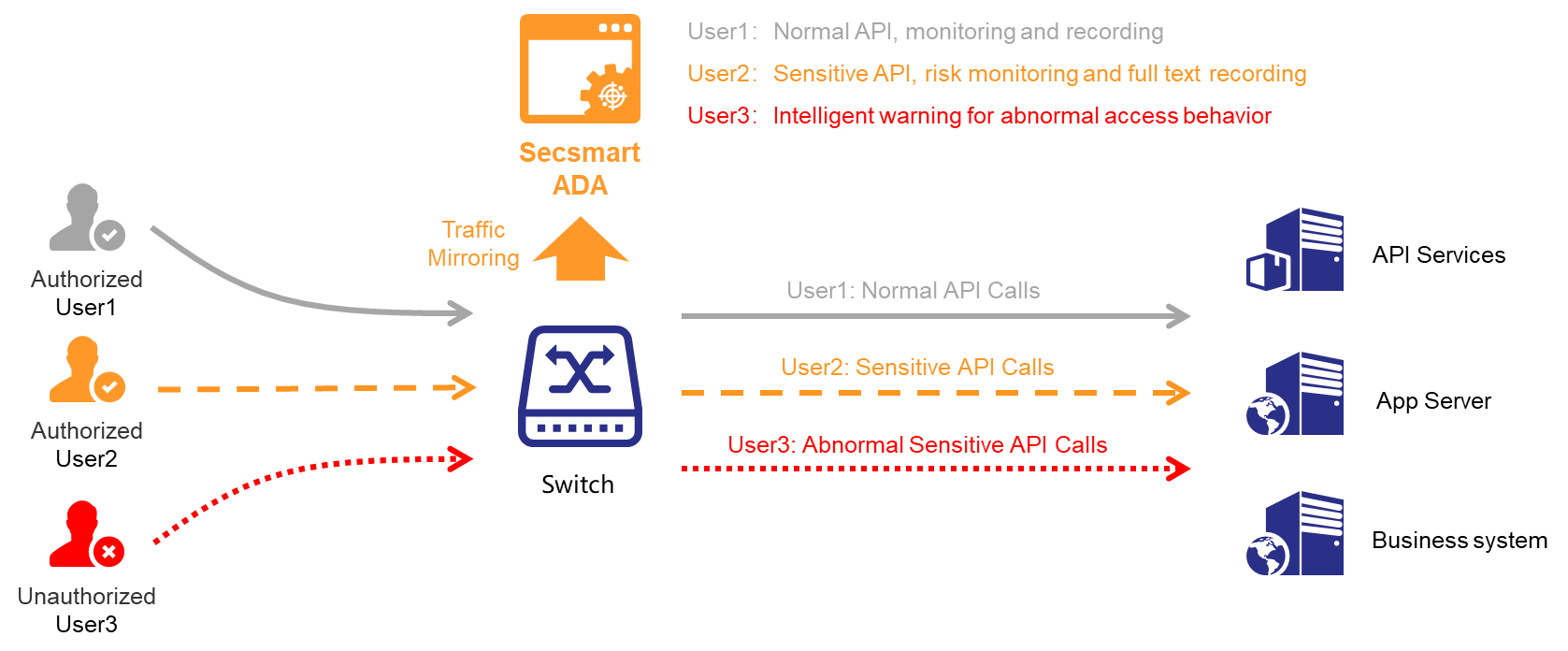
Secsmart Application Data Security Audit Product utilizes two deployment modes: passive and plugin. The "passive listening" deployment mode is used, where it is deployed in the core switch, capturing data traffic through port mirroring. The system uses the Smart Audit Engine for data analysis and alerts, without altering network topology, affecting business data, or changing usage habits. For application systems deployed on public or private clouds, a plugin (Agent) can be used to obtain network traffic from application cloud hosts or proxy servers such as Nginx, achieving parsing of applications/API interfaces.
 |
Product Advantages |  |
Recommended Products
Solutions
Contact Us