|
Product Introduction |  |
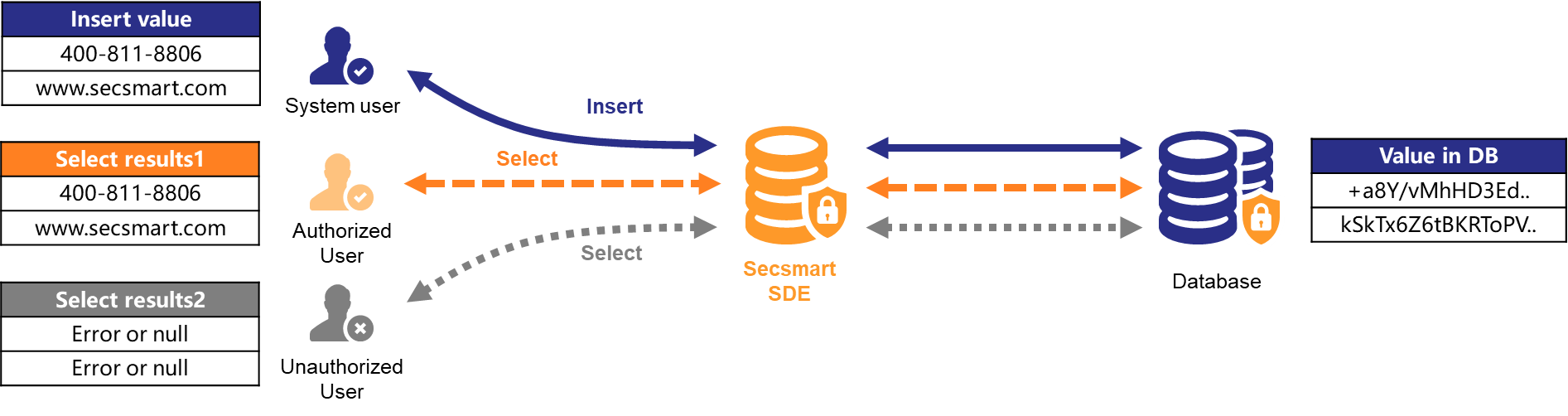
Secsmart Database Encryption is a data security product designed for the encryption of sensitive data in databases and authorized access, which can effectively prevent data breaches caused by the leakage of administrator privileges, loss of data storage media, and hacker attacks. Based on core technologies such as identity authentication, access control, security auditing, and encryption/decryption, anyone or any application accessing encrypted data must be authorized in advance and possess legitimate access rights to access the encrypted data.
 |
Product Value |  |
 |
Deployment Mode |  |
Secsmart Database Encryption Product is a post-proxy system based on database extensions, which can be reached via the customer's database system's routing. There is no need to change the existing system and network topology. After the external device is deployed, the system functions will automatically deploy in the customer's database system without manual intervention, making it simple and fast.
 |
Product Advantages |  |
Recommended Products
Solutions
Contact Us