|
Product Introduction |  |
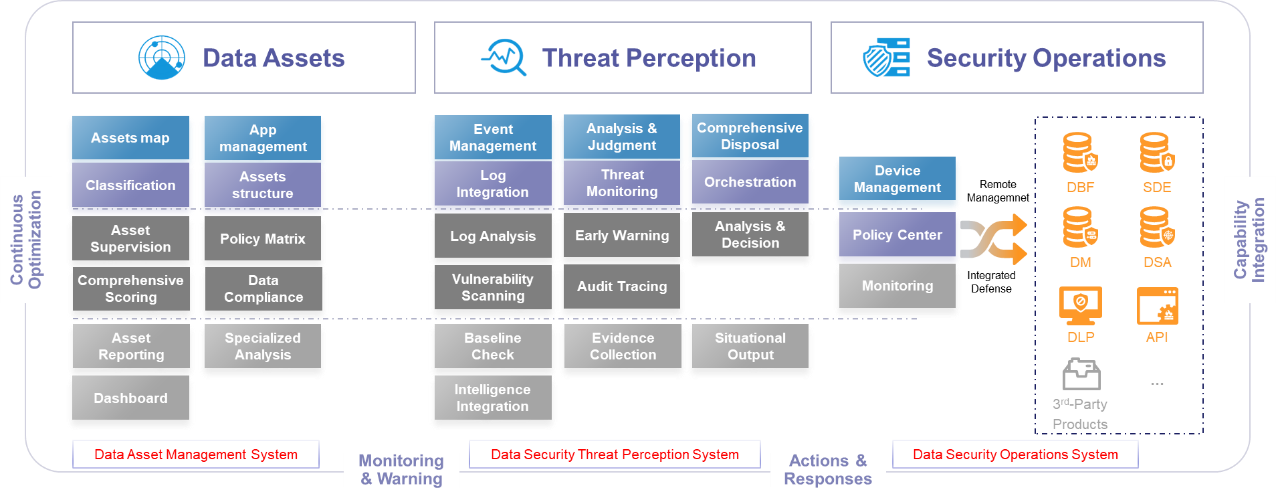
Secsmart Data Security Center is a new generation of data security platform from Secsmart, offering an integration of data asset management, grading, classification, and security capabilities such as masking and encryption. With massive data security data as the core element, it analyzes these elements through big data technology, providing a comprehensive and precise understanding of data security status, enhancing the proactive warning and response capabilities to data security risks, and forming a closed-loop for data security monitoring.
Continuous Data Security Operations
——
Can be used to build a comprehensive data security operations system, assisting enterprises in quickly identifying data asset risks and providing objective, direct, and targeted references for the formulation of data security protection plans and security policies.
 |
Product Value |  |
 |
Deployment Mode |  |
Secsmart Data Security Center is deployed in parallel with various security components and devices. The overall deployment architecture is shown in the figure below:
 |
Product Advantages |  |
Recommended Products
Solutions
Contact Us