|
Product Introduction |  |
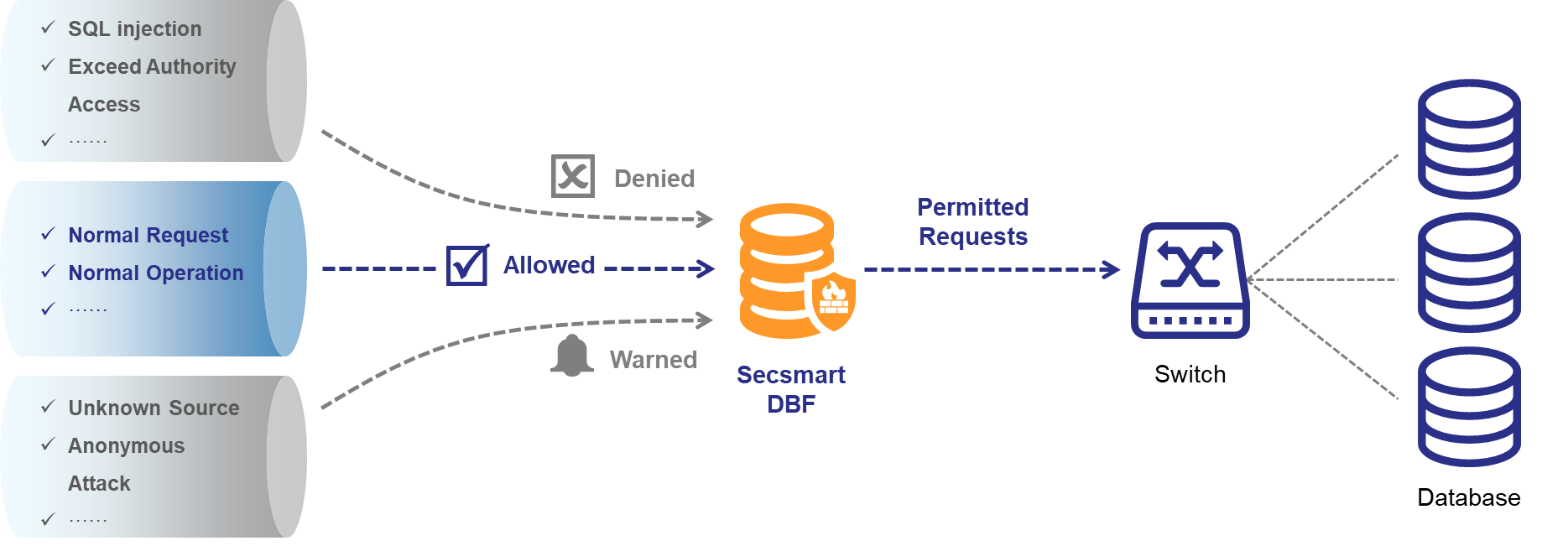
Secsmart Database Firewall Product is a data security product based on database protocol analysis and control of data access behavior. With its built-in database security vulnerability library, it can detect, identify, and block security threats targeting databases in real-time. It achieves control of database access behavior, interruption of high-risk operations, and auditing of suspicious activities, safeguarding the stability of customer business and data security.
 |
Product Value |  |
 |
Deployment Mode |  |
Local Deployment Mode
(1) Transparent Bridge Mode
The database firewall is directly connected between the application server and the database, with applications or users directly accessing the database's address and port.
(2) Proxy Gateway Mode
Applications or users directly access the address and port of the database firewall, which acts as a database proxy, forwarding requests to the database and returning results to the user.
Cloud Deployment Mode
(1) Transparent Bridge Mode
Cloud applications and cloud databases are divided into different virtual subnets, relying on virtual switches (VSwitch) to build a transparent bridge. Cloud applications or users directly access the virtual IP and port of the cloud database, with processing logic similar to local transparent bridge deployment.
(2) Proxy Gateway Mode
Cloud applications or users directly access the virtual IP and port of the database firewall, which acts as a database proxy, forwarding requests to the database and returning resul
 |
Product Advantages |  |
Recommended Products
Solutions
Contact Us