|
Product Introduction |  |
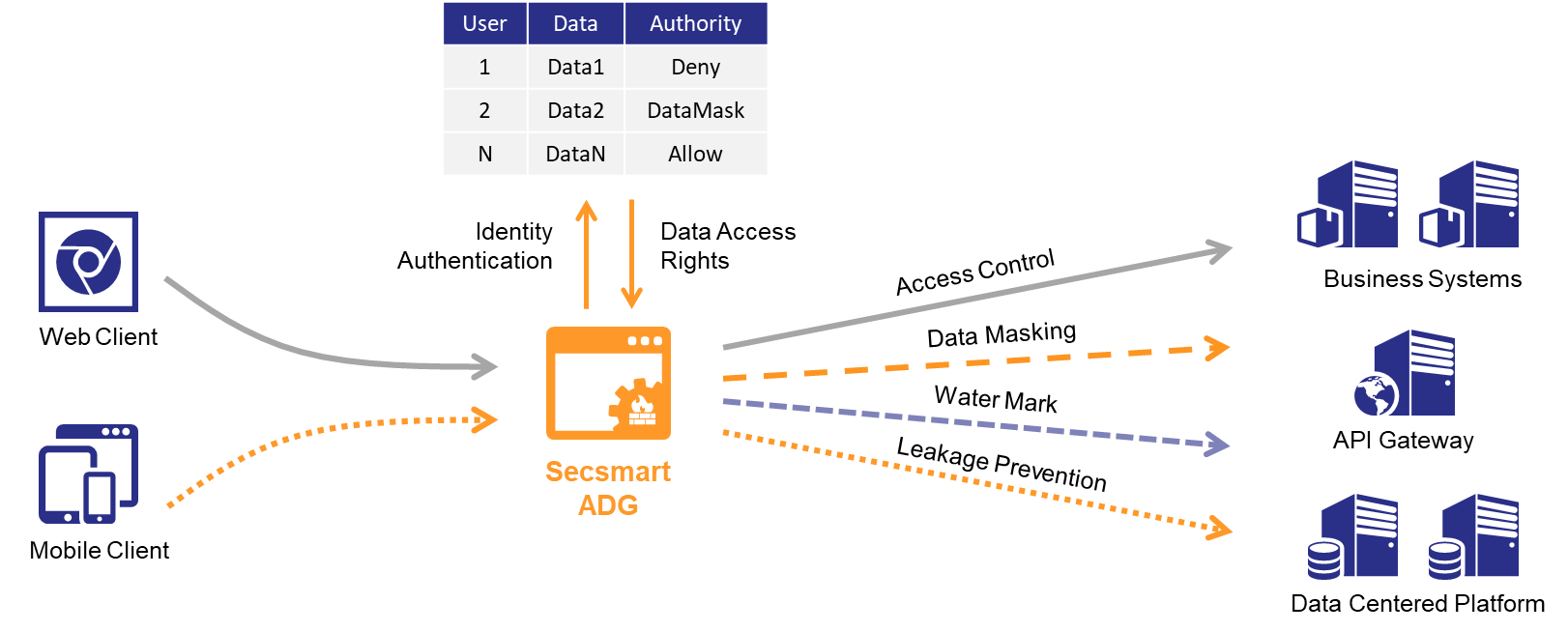
Secsmart Application Data Security Gateway Product can be deployed independently between the application client and the application server, or in conjunction with the data mid-end to provide fine-grained data access control at the application interface (API) level, sensitive data identification, data masking, digital watermarking, dynamic data security protection, security log auditing and risk identification, and situational analysis, among other data security functions. The Application (API) Data Security Gateway simplifies the deployment process, enhances data security operations capabilities, and assists enterprises/organizations in preventing the leakage of sensitive data, meeting application security compliance requirements.
 |
Product Value |  |
 |
Deployment Mode |  |
Secsmart Application Data Security Gateway Product is deployed in proxy mode, giving it the ability to uniformly access applications, protect services exposed by the data mid-end, and avoid the risk of data leakage.
 |
Product Advantages |  |
Recommended Products
Solutions
Contact Us